Reading time: ~ 3 min.

The information security incident management process according to the ISO/IEC 27035-1
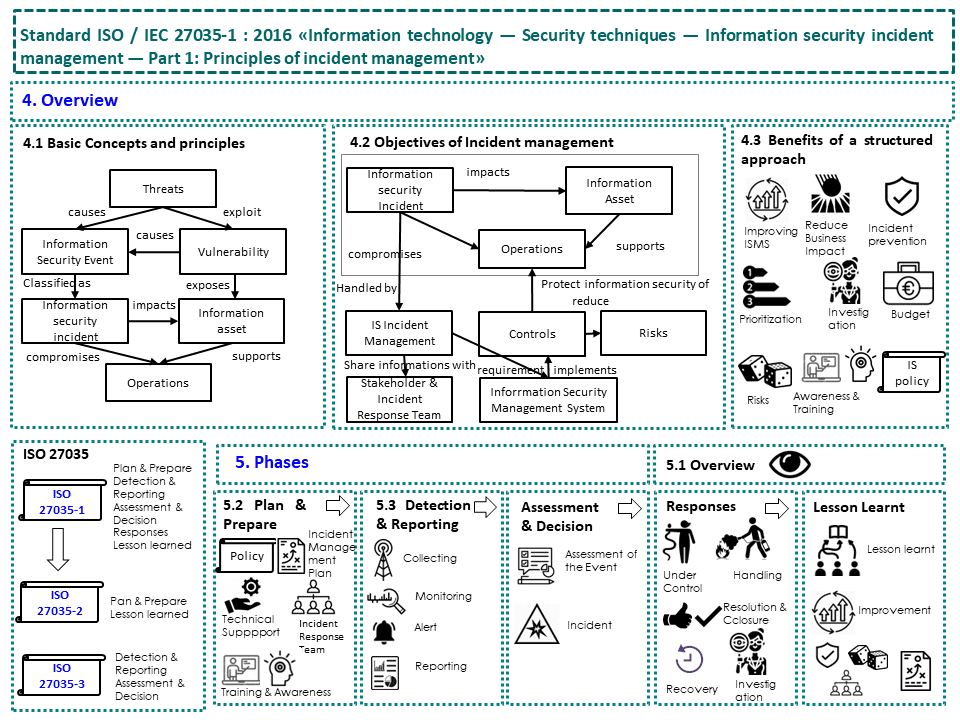
ISO/IEC 27035-1:2016 is indeed the basis of this particular composite International standard on the information security incident management, where you can find essential concepts and the stages on handling this matter.
This ISO/IEC standard combines these concepts with principles giving us a guideline for a clearly defined approch to detecting, reporting, assesing and responding to incident and finally applying the lessons learned.
It is interesting to note that the principles suggested with ISO/IEC 27035-1:2016 can be applied to every organization, regardless its industry, size and nature. The organizations can manage the adjustement of the standard guidance according to their particular context and especially to their information security risk circumstances. This standard can be applied also to the organizations that provide external information security incident management services.
A closer look to the ISO/IEC 27035-1 standard on information security incident management
If you consider the ISO/IEC 27035-1:2016 approach on handling information security incident, you can notice that it includes the following steps:
✅ Detect & report
✅ Evaluate & decide
✅ Respond
✅ Lesson learned
On suggesting the handling management process, this standard recalls moreover these ISO/IEC standards:
✅ ISO 27035-2, standard that provides guidelines for incident response planning and preparedness.
✅ ISO 27035-3, standard that provides guidelines for ICT incident response (detect and report, evaluate and decide, respond).
The incident management and the relation with the management systems standards
The «concept» of incident management it is indeed related to the following management systems:
✅ Information Security Management Systems (standard ISO 27001, Control 5.24, 5.25, 5.26, 5.27, 5.28)
✅ Business Continuity Management Systems (ISO 22301 standard, Clause 8.4)
The incident management and the correlations with data breach requirements
If you think about information security incident management, you can of course immediately put it in direct correlation with the data breaches requirements set by the law on data protection as the European General Data Protection Regulation or the Swiss Federal Act on Data Protection.
The ISO/IEC27035-1:2016 standard on information security incident management