Reading time: ~ 3 min.
The ISMS requirements set by the updated ISO27001 standard
In the last few days, the International Organization for Standardization (ISO) released its last updated 2022 version of the ISO/IEC 27001 standard on the Information Security Management Systems requirements.
Just in case you don't remember it, this update follows the first release (2005) and the revised version (2013) of one of the best known ISMS standard in the industry. What makes this updated ISO 27001:2022 version different from the previous ones?
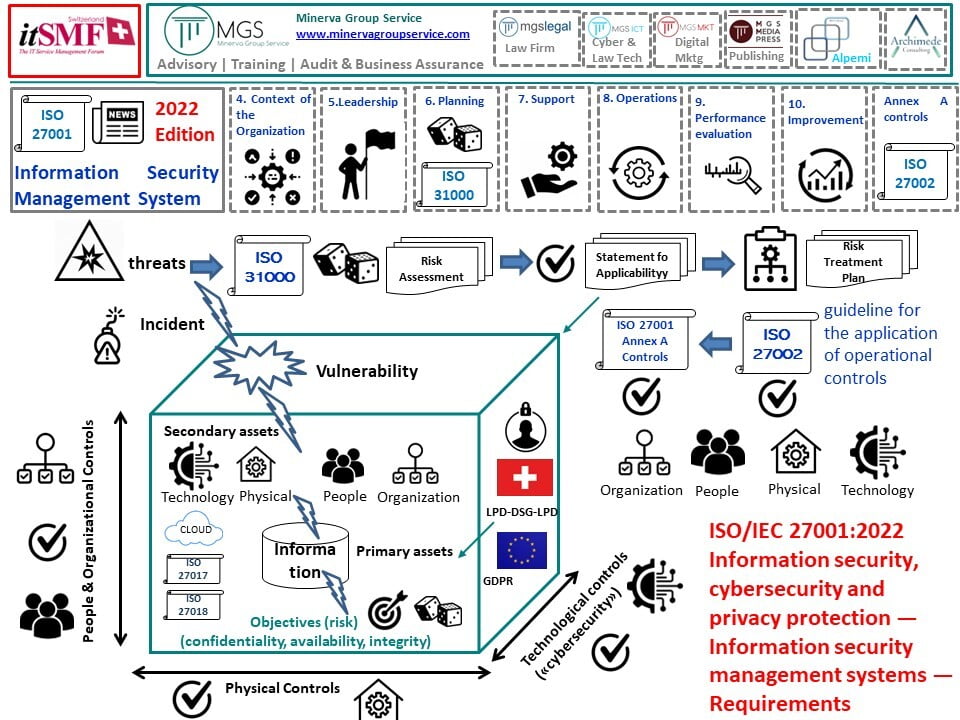
The Information Security Management System ISO27001:2022 and the alignment with ISO 27002
In the age of the rising concerns on privacy and data protection related matters, ISO took advantage of its HSL strategy on the update of its Information Security Management System standard (ISO 27001) aligning it to its 27002:2022 standard.
The Information Security, Cybersecurity and Privacy Protection - Information Security Controls standard (ISO 27002) identifies 4 large groups (clauses or themes) of operational controls:
- organizational controls (organizational aspects);
- people controls (single individual);
- physical controls (physical & environmental objects and aspects);
- technological controls (technological aspects).
I guess we probably can better figure out this approach with the help of this infographic:
The ISO 27002 2022: focus on the control 5.34

The ISO 27002:2022 and the final focus on the controls
At the final stage of our overview on the new Information Security Management System (ISO 27001) update and alignment with ISO 27002, we want to focus on how this last one standard identifies 5 attributes for each single control.
These attributes are different ways of looking at the single control. In particular, the standard defines 5 different views which represent different categorizations of the controls seen from different perspectives:
- Control type (perspective of when and how control changes risk);
- Information security properties (integrity, availability and confidentiality perspective);
- Cybersecurity concepts (perspective of the association of controls to information security);
- Operational capabilities (perspective of operations for information security);
- Security domains (perspective of governance, protection, defense and resilience).
If you don't want to miss our next updates on Information Security Management System, requirements, ISO standards and compliance related matters, don't forget to follow us on our Linkedin Page or subscribe to our newsletter.

